
You probably already know that NKN is a public blockchain powered communication network that allows users and business to share their network connections to create a new internet for everyone to use. However, you may not know all of the amazing technology that we have baked into our solution that make it unique in its open, decentralized architecture. As such, I would like to share with you the 5 elements that make NKN great and even better, why you should care. These five elements are: Decentralized Data Transmission Network (DDTN), Chord Distributed Hash Table (DHT), Proof of Relay (PoR) with Signature Chain, Majority Voting Cellular Automata (MOCA) consensus, and our Incentive Distribution System. In this short article, I would like to give you a rundown of these elements for the everyday man in the street (or for anyone who do not have a degree in cryptography and rocket science).
But first, let me describe to you at a high level, what NKN is and what it is not. NKN is a peer-to-peer overlay network that functions on top of existing network infrastructure. Equipment like routers, switches, fiber backhaul, etc. are vital pipes that allow data to flow. We are not trying to change the underlying architecture of today’s network infrastructure, however, what NKN does do is change the way data is transmitted over those pipes.
The first element is our Decentralized Data Transmission Network (DDTN) . NKN uses a combination of clients and nodes to create a shared network for its users. A Client is an agent at the endpoints of the network that sends and receives data for NKN users. This client software is open source and is small enough to be embedded into mobile applications, IoT devices, wireless gateways, or just about any device or app you use on a regular basis. Nodes, on the other hand, are software agents that run on PCs/laptops, servers, and other infrastructure equipment that relay data for the NKN network. Users and business can use our open source node software to share their network connections and earn reward for doing so. The node software joins other nodes in the network to create a web of nodes that create the backbone of NKN’s transmission network.
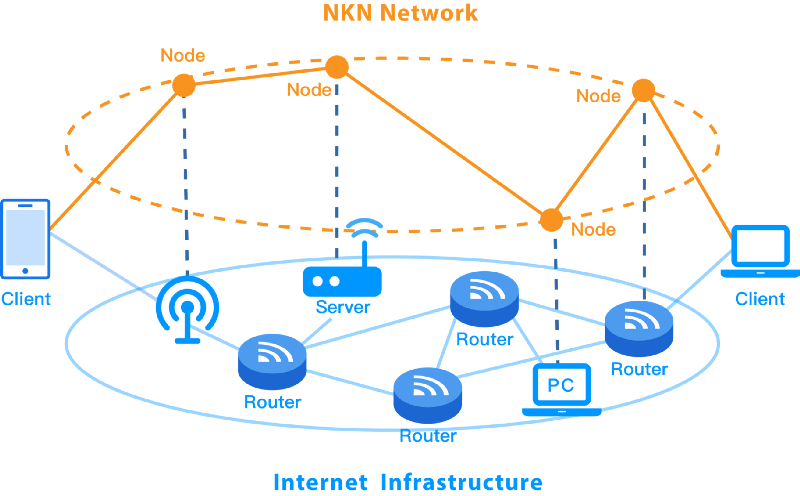
Now that you know more about NKN’s client and node architecture, let us dig a bit deeper into how data is being routed within this architecture. NKN maintains a dynamic topology that allows clients and nodes to join and leave the network at any time. That means users can share network connections when they want to, and can leave the network at will as well. This joining and leaving of different nodes will not affect the overall reliability of the network.
Each time a node joins the network, it is given a new unique NKN address based on factors such as its public key, private key, and current blockchain. The network uses this NKN address to help route traffic via neighbor nodes between sender and receiver. The method that we use for routing is called Chord Distributed Hash Table (Chord DHT) .
You can think of our network as a ring, where nodes are placed on the ring in order running clockwise based on their NKN address (see figure below).
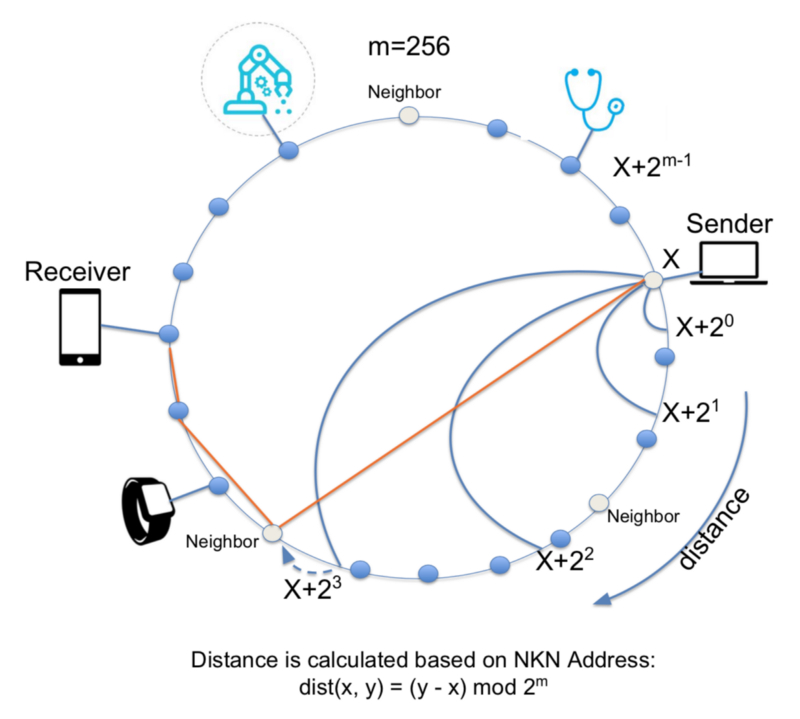
When a sender using NKN’s client sends data to a node in our network, that node will route data to the neighbor that is closest in distance to the receiver. It finds this neighbor by conducting a search in intervals of 2n distance starting from its current location and moving clockwise around the ring. Once it locates the neighbor closest to the receiver it forwards the data. That neighbor node will likewise relay data to its neighbor closest to the receiver, so on and so forth until the data is finally delivered to the receiver .
It’s important to note that distance in this case is based on NKN address and not physical distance in the real world. Why would we do that? It’s because we need to be able to determine a route to transfer your data even when the network dynamically changes as nodes join and leave at any time. By using NKN addresses together with Chord DHT it makes routing verifiable, meaning the choice of neighbors and route are deterministic given all the nodes on the ring.
So far we have covered NKN’s decentralized data transmission network made up of clients and nodes as well as our use of Chord DHT routing. Now, let’s talk about how NKN can send data that is both secure and verifiable using a useful Proof of Work we call, Proof of Relay. Since NKN is a public blockchain powered communication network and not a Sushi restaurant making a really great spicy tuna roll. Our definition of work involves relaying packets for NKN’s network. In addition, we also need a way to prove that nodes were relaying packets on behalf of the NKN network such that we can reward those nodes with incentives. Therefore, Proof of Relay was born.
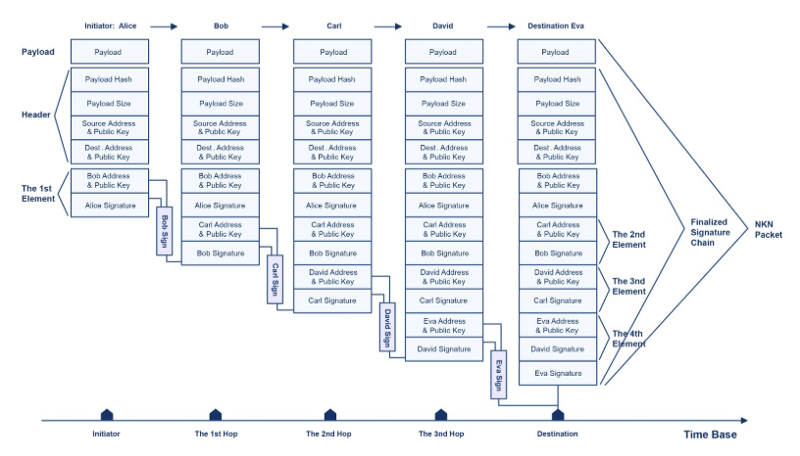
Proof of Relay uses a unique feature created by NKN called a signature chain. Each client or node in NKN’s network has a public key + private key pair that acts as a digital signature to track and validate transactions. When an NKN packet is sent across the NKN network, the client or node uses its key pair to sign the packet and relay that packet to the next node. Each subsequent node will also sign the packet creating a chain of signatures that effectively depends on all previous elements. This makes it impossible for malicious attackers to forge signature chains without access to all private keys in route.
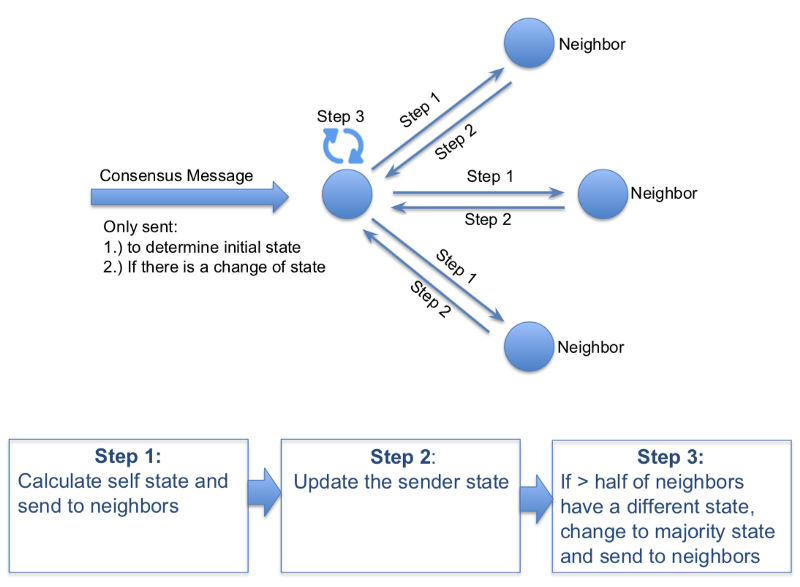
While the signature chain provides a mechanism to verify proof of relay, we still must validate through consensus before we can offer incentive reward for participants. For NKN, we created our own consensus called Majority vOting Cellular Automata (MOCA) . With MOCA, consensus is reached by comparing the state of each node with the state of just a small number of neighbors only, instead of all the nodes in the network. If a majority of a nodes‘ neighbors have a different state, that node will change its own state to the majority state and send an update to its neighbors. This is similar to neighbors in the real world. If your neighbors are SF Giants fans, then you are likely to become a giants fan as well. Consensus is typically reached in just a few iterations < 2–3s, where each iteration is bound by the longest delay in the network (typically <1s) and scalable to millions of nodes. The diagram below shows the 3 steps needed to reach consensus with MOCA.
Finally, the moment you have all been waiting for, the incentive distribution system. How can you earn token rewards for participating in the NKN network? There are really 2 ways: relay reward and mining reward.
Participants who run our node software and relay data on behalf of the NKN network can earn relay reward for doing so. The price is determined between senders and receivers similar to how gas price (transaction fee) works in Ethereum. Furthermore, the reward can be fairly distributed among all the nodes that participated in transmitting the data over the network. From the relayer nodes, a ledger node is selected1 to propose the next block. If successful, the ledger node is rewarded with mining reward.
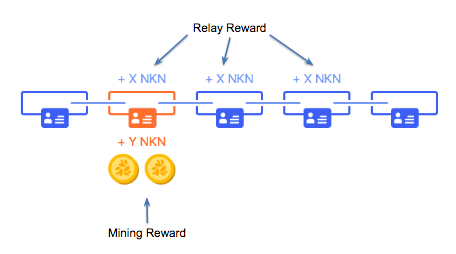
1 Ledger node selection: Lowest Last Signature is used to select Ledger node. Since the signature chain cannot be forged or tampered with and is unpredictable and uncontrollable, Lowest Last Signature is essentially a random selection.
So this is NKN in a nutshell. A distributed blockchain powered communication network made up of clients and nodes overlayed on existing network infrastructure, routed using unique NKN addresses via Chord DHT, featuring packets that contain a signature chain that offers proof of relay, verified by MOCA consensus, and finally relay and mining rewards to participants that are the backbone of our infrastructure. It is this chain of technology that makes NKN open, decentralized, and shared by the community, of the community, and for the community.
