Currently all node-node and client-node traffic are not encrypted. We don’t consider this as a critical issue because:
- Client to client messages are end to end encrypted
- Most node to node messages are signed
- Node to node messages do not contain any info that are not publicly available
However, it’s still beneficial if node-node and client-node messages are encrypted to enhance privacy & more.
Since every node and client has a Ed25519 pk, hop by hop encryption can be easily done using a shared secret key derived sender and receiver’s key. Even better, there are already well implemented and tested libraries (e.g. NaCl/libsodium) in all major languages so it’s quite easy to do it.
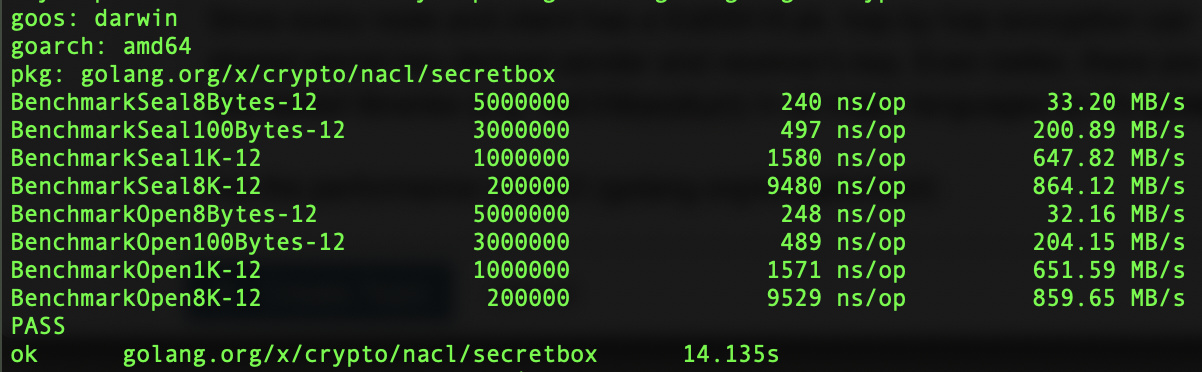
I’ve the performance of NaCl (golang.org/x/crypto/nacl) using one core:
Macbook Pro:
Raspberry Pi Zero W:
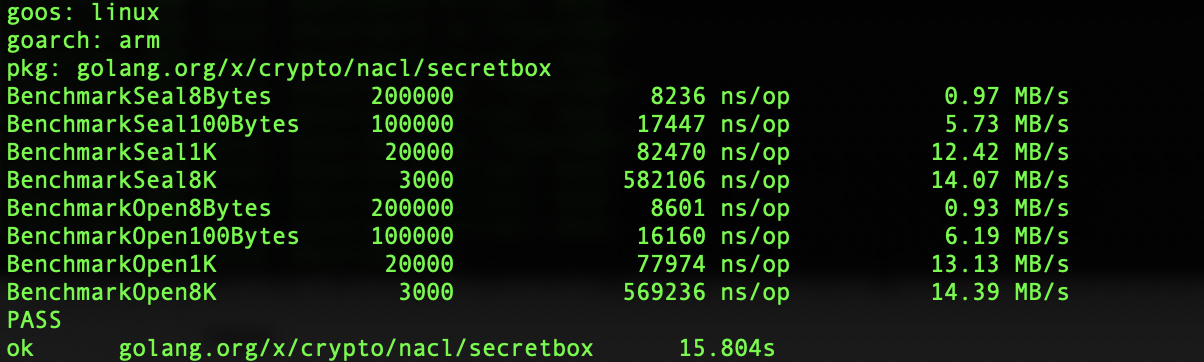
Basically we can do 100k+ or 10+MB/s msg encryption or decryption even on a small raspberry pi zero w, which shouldn’t be the performance bottleneck. (I skipped nacl/box because key derivation only needs to be done once per neighbor)
Another option is to use TLS with Ed25519 public key. This is a more native (and lower level) solution, but it’s not supported in Golang yet. AFAIK the current schedule is to support it in Go 1.13 or later. We need to investigate more to see whether we can use it (e.g. by using the latest Golang repo instead of release).
It’d be good to discuss here about other thoughts or concerns.
